So you are new to the crypto space: you choose a crypto exchange you like, fund your exchange wallet with some funds through bank deposit or credit card, and buy your first crypto. Now, when it comes to withdrawing the crypto, you might need to go through a complicated process where you have to move your crypto around multiple platforms to change it into fiat currencies like USD, and withdraw them. This could be a potentially painstaking process, eating up your precious time and extracting excessive trading fees from you. Millionero is one of the newer crypto exchanges that can make crypto withdrawals easy for you, however.
How does Millionero make crypto withdrawals simple? Let’s find out in this post! But first, the basics:
Crypto Withdrawals: How Do You Withdraw Crypto Funds to Your Bank Account?
When it comes to crypto withdrawals from an exchange platform, you can either send the crypto directly to another crypto wallet you own, or you can choose to turn it into cash and then have the cash sent to your bank account, as there’s no way to withdraw a virtual-only crypto asset as it is to your traditional bank account.
How to perform crypto withdrawals from an exchange to another crypto wallet?
- Open up your crypto exchange wallet.
- You should see a ‘withdraw’ option, under which you might see a ‘crypto wallet’ section that you need to select.
- Select the crypto and enter the amount you would like to withdraw.
- Now you would further be prompted to enter a destination crypto wallet address. Type in the address and confirm your withdrawal.
- The amount should reflect in your crypto wallet soon enough.
Related:Understanding the Basics: What is a Crypto Wallet and How Does It Work?
How to perform crypto withdrawals from an exchange to a traditional bank account?
- Some crypto exchanges themselves allow you to cash out your crypto in one of the available fiat currencies, and directly withdraw them to your bank account.
- For example, in an exchange like Millionero, you can select ‘withdraw’ on your wallet and pick a payment gateway among the available options (such as Coinify, Banxa, Transak, etc.). Let’s say you pick Coinify; now you’ll need to add your bank account and select ‘withdraw’. The funds would reflect in your bank account within 3 working days!
- If your crypto exchange doesn’t support withdrawals in fiat, you may need to use another crypto exchange or third-party broker to sell the crypto you wish to withdraw and turn it into fiat.
- In the aforementioned method, you would need to transfer your crypto from your previous crypto exchange wallet to this new exchange or broker platform, and then choose to ‘sell’ after selecting the fiat currency you would like to withdraw the amount in.
- The funds should reflect in your bank account soon enough.
Now, both this final process of turning crypto into fiat is time-consuming, and requires you to pay extra transaction charges for crypto withdrawals. How can crypto to cash withdrawals be made easy and more efficient? Millionero has a few ideas:
Millionero: How Does it Make Crypto Withdrawals to Cash Easy?
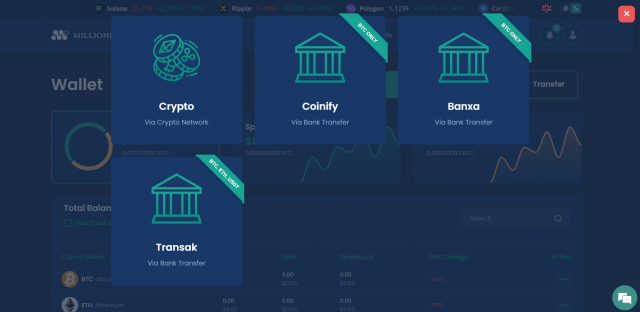
After you have signed up on Millionero, completed the KYC process, and bought your first crypto through the platform, you are provided with multiple options for crypto withdrawals, as shown in the image below:
- Through Crypto Network: You can directly withdraw your crypto through this option to a separate wallet address.
- Through Coinify: This option on Millionero allows you to withdraw your fund in Bitcoin, and can facilitate a bank transfer simultaneously to store an equivalent amount of cash in your fiat bank account. This way, the entire crypto to cash transformation happens in one go through the partnership of Millionero and Coinify.
- Through Banxa: This option also allows you to withdraw your crypto funds in Bitcoin, and initiates a sell window facilitated by the Banxa platform to turn your BTC into EURO immediately, post which, you can withdraw your funds into the bank account you have linked.
- Through Transak: Another platform allowing bank transfers on Millionero, this option lets you withdraw your funds in ETH and USDT along with BTC. After selecting Transak, you’re again prompted to sell your crypto for cash transformation and transfer to your chosen bank account.
With a range of options, Millionero allows for seamless crypto withdrawals and simultaneous transformations into cash in a hassle-free fashion. So how does Millionero make crypto withdrawals easier than most other crypto exchanges? By allowing you to complete the entire crypto to cash conversion in one go, which saves time for you, and by also lowering the overall transaction charges you’d have to otherwise pay.
Sign up on Millionero today to get started with crypto trading! You can further find their socials on Twitter, Instagram, Facebook, and LinkedIn!