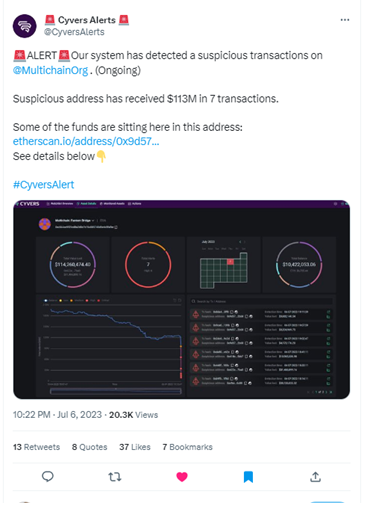
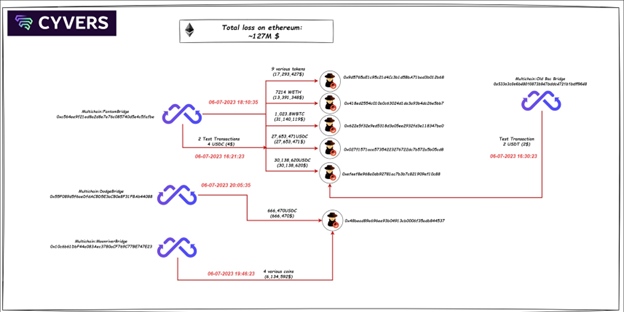
The recent Multichain exploit still hovers around the cryptospace with many unanswered questions. That said, many things contributed to the event, geopolitical considerations aside.
The evolution of web3/blockchain security firms have helped to demystify some of the events that had “god-like” characteristics.
Also the role of continuous AI-driven monitoring processes can’t be ignored.
Deddy Lavid, CEO and co-founder of CyVers,a leading blockchain/web3 security firm explains more.
Deddy Lavid, CEO and Co-founder of CyVers
E-Crypto News:
Please can you tell us about the Multichain exploit?
The Multichain exploit is a stark reminder of the fragility of security in the digital realm. A hacker, or a group, exploited a vulnerability to access unauthorized funds. The incident saw an enormous amount of more than $126 million drained from the protocol.
E-Crypto News:
What were the likely causes of the incident?
The root cause appears to be a compromised private key, leading to an unsanctioned access. This could be a result of a hack, an insider job, or even a rug pull. The truth lies shrouded in the veils of the anonymous cyber realm.
E-Crypto News:
What is unusual about the attack?
This hack displayed an unusual modus operandi. The hackers prepared meticulously, performing three test transactions before the major breach. Then, after the hack, the stolen assets lay dormant, contrary to the usual swift laundering that typically follows such exploits.
E-Crypto News:
What role did CyVers’s processes play in early detection?
CyVers operates on a three-pronged approach – screening, detection, and response. Our AI-driven service is attuned to discern even the slightest irregularities across blockchains, a skill akin to a keen-eyed hunter. In the case of the Multichain exploit, it was our advanced behavioral analysis engine that first noticed the abnormal transactions. The engine works by establishing “normal” transaction patterns and any deviation triggers an immediate alert. As a result, we were the first to detect the break-in, enabling us to alert Multichain and the broader community to stem further losses.
E-Crypto News:
Do you think there are any human elements from an insider perspective in this instance?
It’s conceivable that an insider may have been involved, but such conclusions require more tangible evidence. However, the unique patterns observed point toward the possibility of deeper involvement than a mere external hack.
E-Crypto News:
What are the various inefficiencies that still exist in the Web3 space?
The decentralized nature of Web3 provides freedom but also exposes multiple points of vulnerability. The complexity of smart contracts and the lack of standardized security protocols contribute to a terrain ripe for exploitation.
E-Crypto News:
How can these issues be addressed?
A multi-pronged approach is needed: developing stronger security standards, enhancing smart contract coding practices, and incorporating real-time threat detection systems like CyVers. All that should be combined with regulatory and standardization efforts to make sure the standards we set are being kept across the entire industry.
E-Crypto News:
How have blockchain/Web3 attacks become more sophisticated?
The evolution of blockchain attacks reflects a cat-and-mouse game between technology and its exploiters. Early blockchain attacks were rather direct, employing techniques like phishing and leveraging lax security in wallets. However, with the maturation of blockchain and the growing awareness around basic security measures, the attackers adapted. They developed advanced methodologies, such as multi-chain exploits, deceptive rug pulls, and intricate smart contract vulnerabilities. This has involved sophisticated knowledge of blockchain structures, coding, and even the psychology of panic and greed in the market. The Multichain exploit showed a concerning level of preparation and patience, both hallmarks of this growing sophistication.
E-Crypto News:
What approach do you guys take at CyVers?
We blend the power of AI and blockchain technology to create a proactive, real-time threat detection system. We’re not just passively observing, we’re actively protecting the Web3 universe.
E-Crypto News:
Is the blacklisting of hacker addresses enough? What more can be done?
While useful, blacklisting addresses isn’t a panacea. It’s a reactive measure. We must focus on preemptive actions, creating more secure protocols and fostering global cooperation to combat these issues.
E-Crypto News:
Are MPC wallets safe? Can they be hacked?
Multi-party computation (MPC) wallets are a response to the vulnerabilities that traditional wallets face. In a traditional wallet, the control of assets is tied to a single private key. If this key is compromised, the assets are at risk. However, an MPC wallet uses a protocol that allows multiple parties to jointly generate and manage the private key. It provides a solution that ensures no single point of failure. Even if a participant is compromised, the overall security of the wallet remains intact. This security feature is becoming increasingly important as we move towards a more interconnected and collaborative Web3 space.
Like all aspects of Web3, MPC wallets aren’t impervious to attacks. While they offer increased security, continued vigilance and advancements in security measures are vital.
E-Crypto News:
What precautions can developers and users take to forestall attacks?
Users must stay informed, use trusted platforms, and protect their keys. Developers, meanwhile, need to follow best coding practices, perform rigorous audits, and integrate advanced security tools such as Cyvers VigiLens and AddressShield.
Related:The Rise Of Crypto Hackers And The Best Ways To Steer Clear Of Them
E-Crypto News:
How have blockchain attacks evolved so far?
Initially, attacks were direct and simple. As the technology matured, so did the malfeasance, with more sophisticated multi-chain attacks, deceptive rug pulls, and complex smart contract exploits.
E-Crypto News:
How does the CyVerse engine work?
Our engine employs AI to scrutinize blockchain activities. It acts as a watchful sentinel, alerting us to potential threats in real time.
E-Crypto News:
How can the development of effective regulatory processes improve blockchain/Web3 security?
A laissez-faire approach to blockchain security is no longer tenable given the financial and reputational implications of hacks. The Web3 space needs to embrace a regulatory environment that fosters security and trust. Effective regulatory processes need to be two-fold. First, we need a universal standard of security practices across the blockchain space, a standard that covers every facet from smart contracts to multi-chain protocols. Second, we need robust mechanisms to enforce these standards, to ensure they’re more than just lofty ideals. Regulation doesn’t necessarily mean stifling innovation; it means creating a secure foundation upon which innovation can flourish without undue risk.
E-Crypto News:
How will cooperation within the cryptospace help mitigate risks?
The cryptospace is vast and varied, yet we are all united in a common goal – to make blockchain technology a secure, accessible, and trustworthy foundation for a new digital era. By cooperating, sharing insights and pooling resources, we can fortify our collective defense against malicious actors. I’m optimistic about this collaborative spirit in the cryptospace, and I believe it will drive us forward towards a safer, more secure future. The potential of what we can achieve together is unparalleled, and I am thrilled to be part of this journey.
E-Crypto News:
What are the best steps to secure smart contract code?
Code audits, bug bounties, and the use of formal verification methods can ensure the solidity of smart contracts. But without threat detection systems like CyVers, that offer an extra layer of security, they are much easier targets for attacks.
E-Crypto News:
How can network bridges mitigate risks?
Bridges in Web3 are points of connection that enable transactions between different blockchains. However, these can also become points of vulnerability if not adequately secured. At CyVers, we offer a suite of security products tailored to secure these critical points of interaction. Our behavioral analysis engine, for instance, monitors transaction patterns on these bridges in real time and can quickly identify any abnormalities. Additionally, our Cyber Incident Response team is always ready to respond to any detected threats, ensuring that our clients’ assets remain safe and protected. Our tools are like the vigilant watchmen of these bridges, standing guard to ensure a safe and seamless flow of transactions.
E-Crypto News:
What are your blockchain security projections for the next five years?
-
-
Regulation will play a pivotal role: As the blockchain industry matures, it’s inevitable that we’ll see increased regulatory involvement. Policymakers are becoming more attuned to the intricacies of blockchain technology and the need for effective regulation to ensure security, consumer protection, and fair competition. We foresee global regulatory bodies creating comprehensive frameworks that will promote transparency, accountability, and integrity within the blockchain ecosystem. This won’t stifle innovation; instead, it will pave the way for greater trust and wider adoption of blockchain technologies.
-
Increased detection and stability: As security measures evolve, we will witness a significant improvement in the detection capabilities of cybersecurity platforms. This evolution will be driven by advancements in AI and machine learning, enabling platforms like CyVers to identify potential threats in real-time, thus significantly increasing the stability of web3 protocols and applications.
-
Fewer hacks: With improved detection capabilities and enhanced security measures in place, the frequency of cyber-attacks will dramatically decrease. While it’s unlikely we will ever eliminate hacks completely, the combination of proactive security measures, robust response mechanisms, and regulatory oversight will make successful attacks a rarity rather than a norm.
-
Effective measures for containment and mitigation: When incidents do occur, the response will be swift and decisive. Cybersecurity platforms will have real-time response mechanisms that can swiftly contain an attack, minimizing the potential damage. We’re already seeing the development of tools that can freeze assets and blacklist addresses following an attack, and this will become standard practice.
-
Mass adoption of blockchain technologies: All these developments will culminate in paving the way for mass adoption of blockchain technologies. As people and businesses become more confident in the security of blockchain, we will see its application in a wide array of industries, from finance and healthcare to supply chain management and beyond. At CyVers, we’re thrilled to be at the forefront of these changes, ensuring the safe and secure growth of the blockchain ecosystem.
-
Related: Finance with Artificial Intelligence